HIPAA Compliance Without the Theater
HIPAA is forgiving about technology choices but unforgiving about discipline. That is especially true for electronic protected health information, ePHI. The rules are technical. In practice, they require covered entities to know where ePHI lives and to understand how it moves, both on paper and in daily operations.
Start with status. If you are a provider, health plan, or clearinghouse that transmits health information electronically, you are a covered entity. If you touch PHI for one of those entities, you are likely a business associate. Either way, the baseline is the same: protect the confidentiality, integrity, and availability of ePHI through administrative, physical, and technical safeguards.
Leaders who get this right move on two fronts, contract hygiene and operational controls. Every upstream or downstream partner handling PHI needs a business associate agreement that says what gets shared, how it is protected, and what happens when things go wrong. Then you run the program you just promised.
HIPAA expects an operational security program that runs every day, not a stack of policies on a shelf. Risk analysis and risk management are continuous, not annual chores. Inventory every system that creates, receives, maintains, or transmits ePHI. Test how those systems could fail. Decide, in writing, what you will accept, mitigate, or retire. Document sanctions for noncompliance. Review audit logs.
When HHS arrives, these basics are the first things they ask for, and missing them is what turns an incident into a settlement.
Most breaches start with ordinary behavior, so training must change how people work. Staff click links, reuse passwords, and share access unless you teach and measure better habits. A lightweight program that sends periodic reminders, runs phishing simulations, and enforces password and login monitoring rules will reduce risk more than any glossy binder. Train when people join, retrain when roles or policies change, and record that it happened.
Two common breach patterns deserve special preparation. Ransomware locks your systems and demands payment, while account takeover occurs when an attacker signs in as a legitimate user. The practical countermeasures are well known, even if they take discipline to maintain: multifactor authentication wherever you can support it; encryption in transit and at rest where reasonable; timely patching; alerting that someone actually reads; and a tested incident response plan with names, phones, and escalation paths. When a bad day arrives, your team executes, law enforcement is looped in, indicators are shared with the right channels, and breach notifications follow the clock.
Risk often lives outside the electronic health record, or EHR, in tools that seem nonclinical but still touch patient information. Public website trackers, patient apps, cloud tools, and a growing vendor list can capture identifiers tied to health context. Treat pixels, SDKs, and analytics tags as systems that may handle PHI. Run them through risk analysis, access controls, and business associate agreements when required. Assign an owner to inventory these tools, and revisit the list whenever marketing or product ships something new.
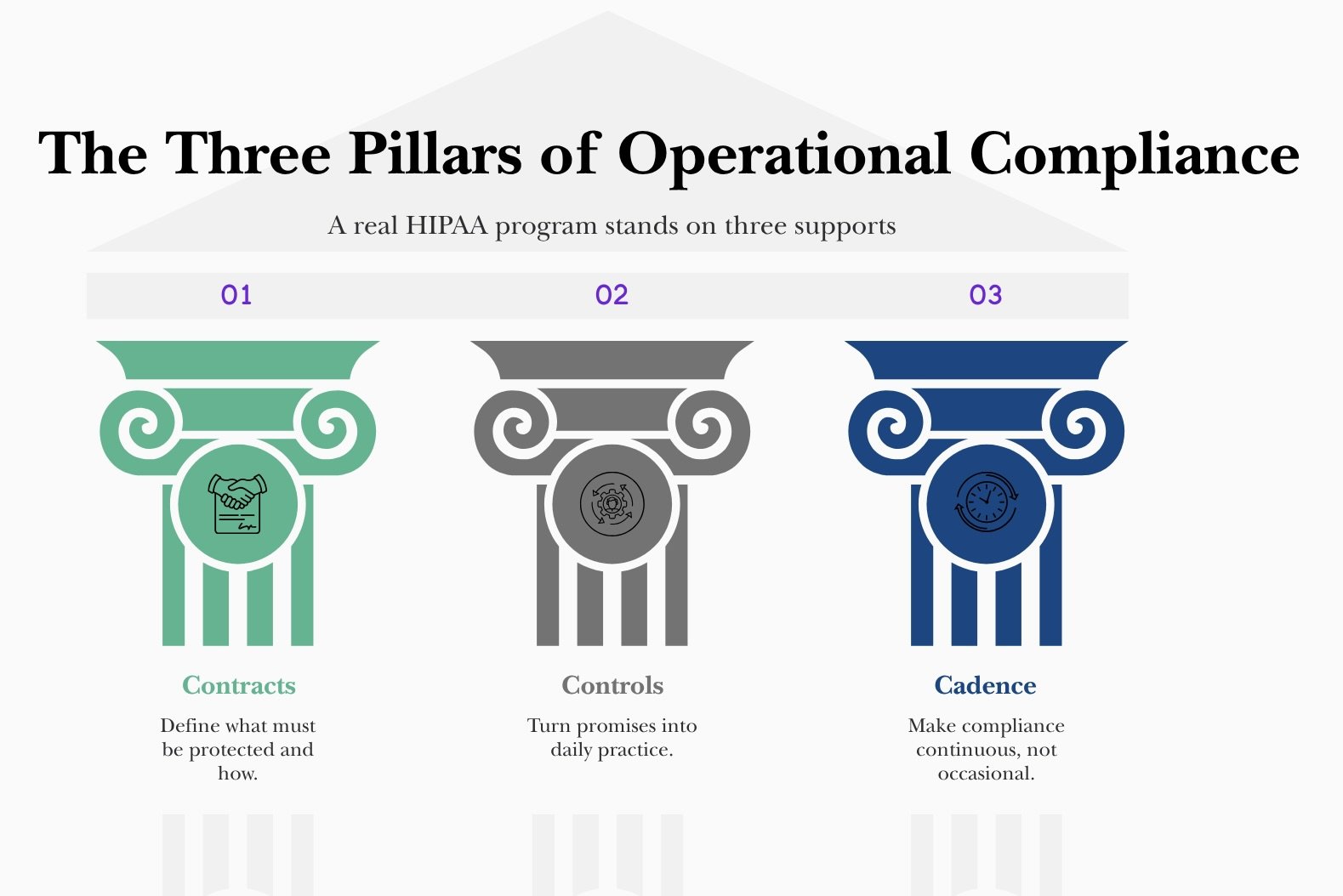
Compliance manifests through contracts, controls, and cadence. Contracts mean BAAs that are specific on duties, breach cooperation, and audit rights. Controls mean the administrative standards that carry the weight: assigned security responsibility, workforce security, access management, training, incident procedures, contingency planning, and periodic evaluation. Cadence means reviews that track environmental and operational change, not just calendar quarters. This is the quiet excellence HIPAA expects, and it is where most investigations land.
Together, they prove your program is real — not just paperwork.
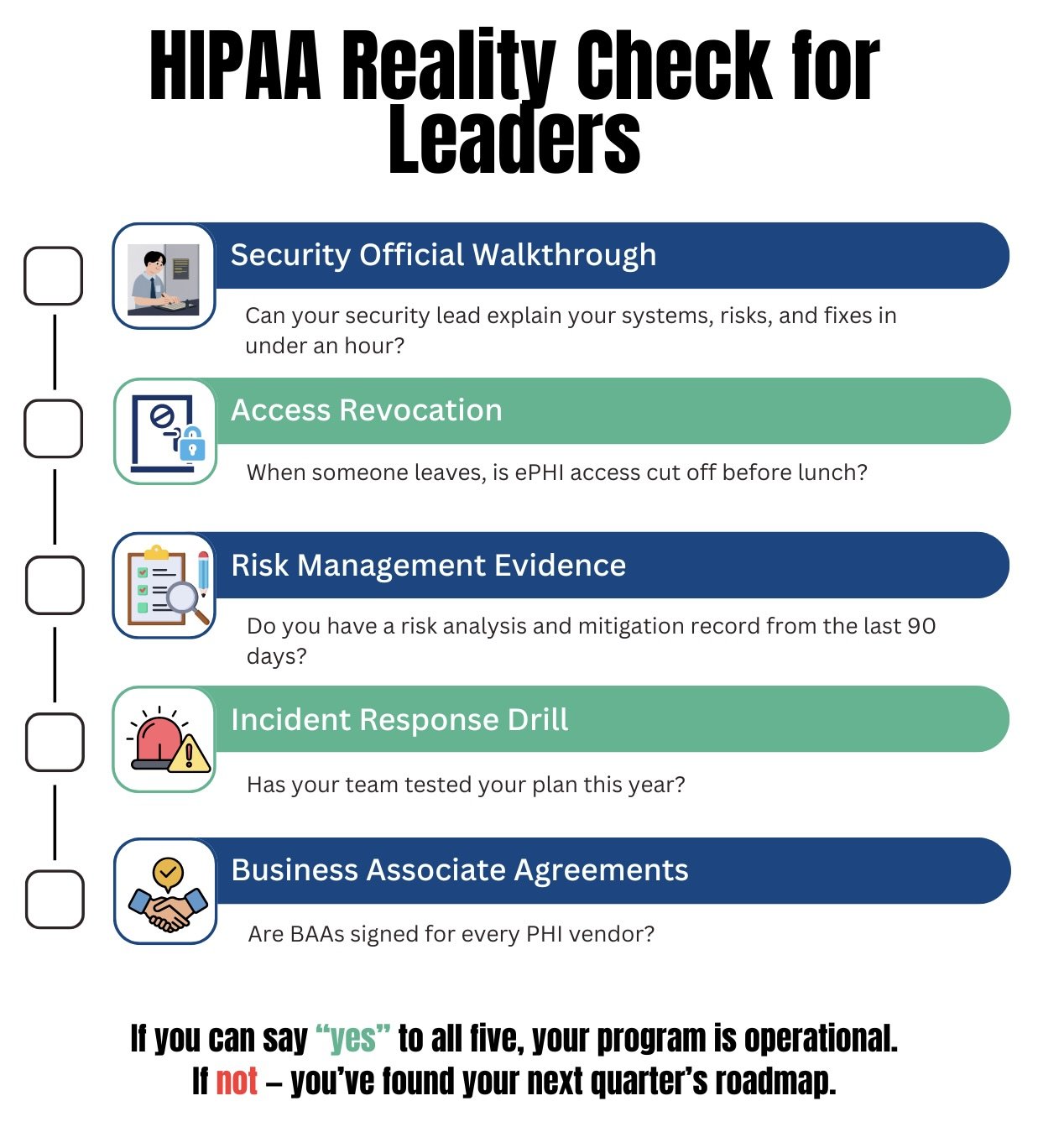
Two closing tests help leaders gauge whether the program is real. First, could your security official walk a new auditor through your environment in an hour, systems, data flows, risks, and recent fixes, using current documents? Second, could a departing employee lose access to every system with ePHI before lunch, and could you prove it?
If the answers are yes, you are doing the work. If not, you have your next quarter’s roadmap.
Use this checklist to create your next quarter’s roadmap.